Retain data integrity with cryptographic checksums
What are cryptographic checksums? Why are they important to network and data security? How can you use them to ensure you are running the correct firmware on your networking devices? Read on and find the answers to these questions and more.
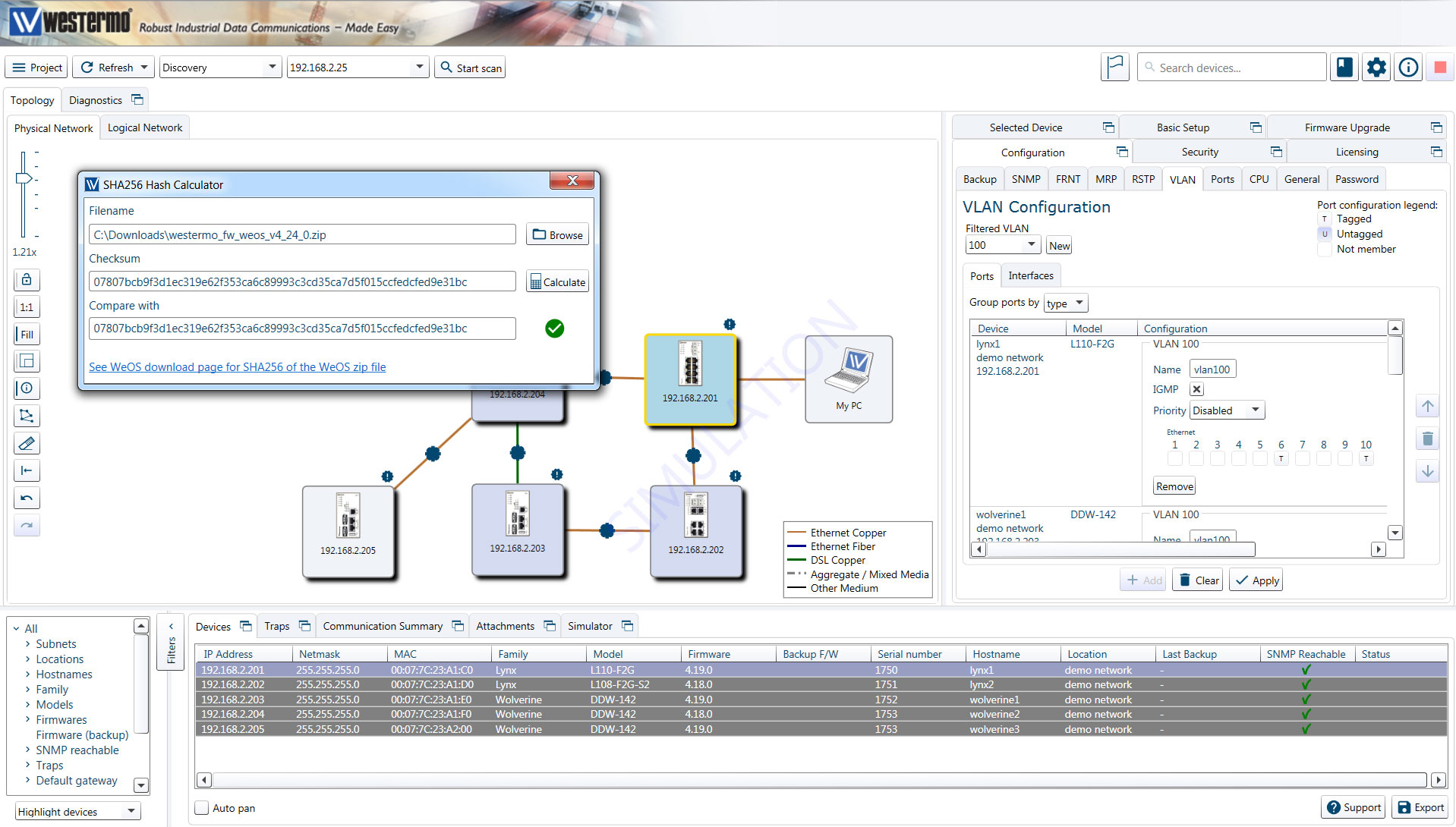
Let’s dive straight into what a cryptographic checksum is, or as they are often called, a cryptographic hash. A hash is like a signature for a data file and is the result of a mathematical function that maps data of arbitrary length to a fixed string of digits. This ensures that for every input, you get a unique output (unique hash) and because the hash function is designed to be `one-way’ and infeasible to invert, it is impossible to calculate the input from the output. This means that you can verify whether received data has been tampered with.
By comparing the hashes you can confirm whether a firmware image for WeOS is an officially published version from Westermo. To do this you simply need to calculate a SHA-256 hash of the firmware image and then compare it to the official hash for the firmware available on the Westermo website. To make this easier, the procedure will be supported by WeConfig 1.9. The exact process is shown in the video below.
As is always the case with cybersecurity, successful implementation involves a combination of people, processes and technology. It may be necessary to establish a process whereby firmware upgrades are only performed after a checksum or hash check has taken place.
This will provide greater protection from phishing, where an attacker tries to get you to install a `false’ firmware. Performing a firmware installation in his way removes the distribution of the firmware from the integrity chain. This means there is no longer a need to verify the source of the firmware every time, you only need to compare the hashes.

Niklas Mörth
Cybersecurity Product Manager
Nuri Shakeer
International sales

Bitte nutzen Sie für Supportanfragen unser Support Formular
